2023-06-06 - github personal readme
recently i've listened to i'm the real Connor episode of darknet diaries. TL;DR version is that guy found himself in a situation, where his (very reach) github profile was used by a different person, to get to a job interview (i.e. “look at all my great work” – except it was some1 else's profile).
it got me into thinking – how could it be prevented? obviously HR person could just ask for a specific commit on a private repo, shared with this person. this way it can be proven that the person has R/W access there. a bit of a fuss for both sides, but doable. is there any passive way?
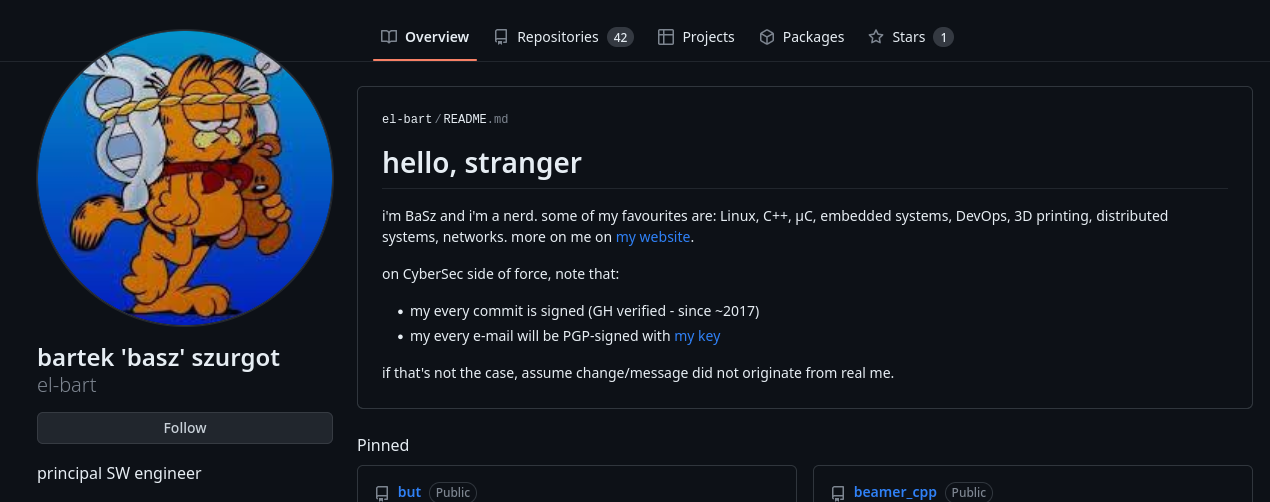
how would u then warn recruiter… or in fact – any other person that want to verify you is you? what crossed my mind is GPG keys (that i use for year now) and a github note, clearly visible on a main profile. turns out github allows to add private notes, that are always visible on the main page. it's just a bit “hidden feature”, as one must create a repo, named the same as the account, and put a README.md there. once done profile looks like this:
now this is loud and clear warning, for other side to detect sth is fishy (eg. unsigned e-mail, or e-mail signed with a different key). it's also verifiable w/o owner being actively involved. last, but not least – it just looks nice. :)
you might have noticed i've also mention commits are being signed, too. that's another topic. supply chain attacks are getting more and more common in FOSS world. possible attack vector here is: account being taken over. if this happens, how can users tell if commit / release is legit? again – GPG comes to a rescue. with each genuine commit being signed, it's easier for others to spot a problem and rise alarm.